In mid-April 2025, a highly sophisticated phishing attack targeted Gmail users, taking advantage of weaknesses in Google's own systems to achieve unprecedented levels of deception.
This recent Gmail phishing campaign was particularly insidious. It mimicked real Google alerts – security warnings, legal notices, and even subpoena messages – to trick users into clicking malicious links. The emails looked like they came from official Gmail addresses, and the websites they linked to? It's hosted on sites.google.com. To the average user, everything seemed legit. Even technical users could be fooled.
So what happened exactly? How did this attack bypass defenses? What can you do now to avoid being a victim? In this article, we break it all down – clearly, technically, and practically.
The Recent Attack on Gmail Users – What Happened
This Gmail attack gained significant public attention when people who were targeted shared what happened. Most notably – the X post of Nick Johnson (founder and lead developer of the Ethereum Name Service (ENS)). On April 16th, 2025, Johnson wrote about his experience on X (formerly Twitter), describing an "extremely sophisticated Gmail phishing attack" that exploited vulnerabilities in Google's infrastructure.
He shared the email he received, which looked like a real security alert from Google about a subpoena for his account data. The first reports made the cybersecurity community and Gmail users pretty worried because the phishing emails looked real and had passed the usual authentication checks.

Key Characteristics of This Gmail Phishing Attack
- ⚠️ Legitimate Sender Address Spoofing: Emails appeared to originate from official Google addresses, such as no-reply@google.com or no-reply@accounts.google.com.
- Authentication Bypass: The phishing emails successfully passed DomainKeys Identified Mail (DKIM) signature checks, a standard method for verifying email sender authenticity. This meant Gmail's systems did not flag the emails as suspicious based on this check alone.
- ⚠️ Inbox Integration: Due to passing authentication checks, the malicious emails were often grouped within the same conversation thread as legitimate security alerts from Google, further reinforcing their perceived authenticity.
- Convincing Lures: Attackers used social engineering tactics, like alarming subject lines and content, such as fake notices about legal subpoenas requiring the release of account data or urgent security alerts demanding immediate user action.
- ⚠️ Exploitation of Google Infrastructure: The campaign used Google's own platforms in a unique way, hosting the credential-harvesting landing pages on the sites.google.com domain.
How Hackers Wore Google’s Own Clothes: The Spoofing Mechanism
This incident wasn't just down to one thing. Instead, it happened because they managed to chain together a bunch of vulnerabilities or weaknesses across different Google services. The attackers combined the misuse of the old Google Sites platform with the way Google's OAuth system was used, and took advantage of specific behaviours related to DKIM signature handling, particularly in email forwarding situations.
This combination made a really powerful attack, which wouldn't have been possible by exploiting any one thing on its own.
Fake Google Subpoena/Security Alerts
Imagine receiving an email that says your account is under investigation. Or that someone has accessed your Gmail from a suspicious location.
The most dangerous part of this Gmail attack is psychological. The attackers play on urgency and authority. Whether it is a fake legal notice or a warning of a data breach, the goal is to make you act before thinking. And because everything looked Google-approved, many users do.
Leveraging Google Sites for Malicious Hosting
Clicking the link in the email often leads victims not to a random dodgy domain, but to a webpage built using Google Sites (sites.google.com/...). This is clever because the google.com part of the address lulls people into a false sense of security.
The main problem with the old Google Sites platform was that it could support any kind of script or embed. This meant that attackers could easily create and host pages that looked like Google's official sign-in page but were actually designed to steal your details.
People often said these pages were "very convincing" or an "exact duplicate" of the real Google login page. The only way you'd spot the difference is if you were really paying attention, and that's the URL in the address bar showing sites.google.com instead of accounts.google.com, which is what you see when you're actually signed into a Google account.
DKIM Replay and OAuth Manipulation
Let's get a bit technical here.
DKIM (DomainKeys Identified Mail) is an email authentication method that uses cryptographic signatures to verify messages. Normally, this prevents spoofing. But the attackers replayed previously signed messages – intercepting a valid DKIM signature and reusing it on a phishing email.

Think of it like someone copying a perfectly valid digital signature and pasting it onto a fake contract. To verification systems, the signature checks out – even though the content is malicious.
Some signs even point to OAuth manipulation, where the attackers may have used compromised tokens to impersonate legitimate users or access email content.
A great resource to read more about the tech behind this attack: Google Spoofed Via DKIM Replay Attack: A Technical Breakdown
Impact and Significance: Why This Attack Matters
When a Gmail attack uses Google’s own services to deceive users, the implications are far-reaching. This isn’t just about email phishing anymore. It’s about trust – trust in one of the most powerful tech ecosystems in the world being shaken at its foundation.
Let’s be clear: anyone can fall victim to Gmail phishing when malicious content is hidden behind Google’s own domains. Your browser doesn’t warn you. Your antivirus doesn’t blink. Even corporate security systems might let it slide. Why? Because the phishing pages are hosted on Google. The message passes DKIM. It all looks legit.
And that’s exactly what makes this one of the most Gmail sophisticated attacks we’ve seen.
Potential Consequences for Victims
- Credential Compromise: The immediate goal is often stealing your Gmail login details.
- Total Account Takeover: With your password, attackers can potentially lock you out, change recovery information, and gain full control.
- Data Exfiltration: Access to your Gmail means access to potentially years of sensitive emails, contacts, attached files stored in Google Drive, photos, and more. Imagine private conversations, financial documents, personal plans – all exposed.
- Financial Theft: If your Gmail is linked to financial accounts, or if attackers find banking details within your emails, direct theft becomes a terrifying possibility.
- Identity Theft: Personal information gleaned from emails can be used to impersonate you elsewhere.
- Launchpad for More Attacks: Your compromised account can be used to send further Gmail phishing emails to your contacts, exploiting their trust in you.
A compromised Google account often functions as a "skeleton key" to a significant portion of a user's digital life. This is because Gmail's central role not only within Google's extensive ecosystem (Drive, Photos, Calendar, Pay) but also its frequent use as an identity provider for logging into countless third-party services via "Sign in with Google" functionality.
This Gmail phishing attack should concern everyone who relies on traditional email services for anything important – which is nearly all people. The integrity of email communication depends on authentication protocols and trusted services. When attackers manipulate both, the result is chaos.
The fact that attackers were able to exploit trusted infrastructure without setting off alarms shows just how urgent it is to rethink the foundations of email security. Traditional spam filters, firewalls and browser warnings just aren't enough these days. Users, businesses and even governments are all at higher risk now.
The Domino Effect: Connections to Other Recent Incidents
This Gmail spoofing campaign did not occur in isolation but in line with several ongoing trends in the cybersecurity threat landscape:
- Increasing Phishing Sophistication & Brand Impersonation
This attack is a perfect example of the general trend towards more sophisticated and convincing phishing emails, which are increasingly difficult to distinguish from legitimate communications. Attackers are getting smarter about exploiting technical vulnerabilities and psychological biases.
Recent Example: PayPal Phishing Scam Emails
There were some ongoing campaigns in spring 2025 where scammers sent emails that looked really convincing and appeared to be from PayPal. They used tactics like fake invoices for large sums or urgent "account security" alerts, often including dodgy phone numbers, to try and panic users into revealing their details or getting in touch with the scammers directly.
- AI-Enhanced Threats
One more trend elevating modern email threats is the increasing use of Artificial Intelligence. Experts and agencies have noted AI's power to craft flawless, personalized phishing emails or generate deepfake audio, making attacks even more deceptive.
Recent Example: AI-Powered Gmail Phishing Attacks
- MFA Bypass Techniques
Attackers are actively developing and deploying techniques to bypass MFA. Examples include the Astaroth phishing campaign observed in February 2025, which used Man-in-the-Middle (MiTM) phishing kits to steal both passwords and MFA codes in real-time , and the rise of Phishing-as-a-Service (PhaaS) platforms like Tycoon 2FA, designed specifically to defeat MFA for services like Microsoft 365 and Gmail. The prevalence of such tools highlights the limitations of relying solely on traditional MFA methods.
- Ransomware's Enduring Threat via Email
It's really important to keep in mind that email is still a top way for ransomware to spread. While one type of threat is always in the news, others carry on, often using the same basic methods of getting in, like sending out emails that are designed to trick people.
Recent Example: Medusa Ransomware
Medusa's way of getting into a system can change, but security reports from Q1 2025 show that a lot of ransomware infections start with a dodgy email – maybe a dodgy attachment or a link to the malware.
- The Rise of MFA Bypass Techniques
As Multi-Factor Authentication (MFA) becomes standard, attackers are focusing intensely on ways to defeat it. Techniques like "MFA fatigue" (spamming users with prompts), session hijacking (stealing active login cookies), or exploiting account recovery processes are becoming increasingly common tools in the arsenal for sophisticated email attacks.
Recent Example: Astaroth phishing campaign
In February 2025 we saw the Astaroth phishing campaign, which used Man-in-the-Middle (MiTM) phishing kits to steal passwords and MFA codes in real-time. And then there's the rise of Phishing-as-a-Service (PhaaS) platforms like Tycoon 2FA, which are designed to defeat MFA for services like Microsoft 365 and Gmail. The fact that these kinds of tools are so common shows that we can't just rely on the usual MFA methods.
How to Detect and Avoid Such Attacks
This sophisticated Gmail attack makes it feel nearly invisible – but there are ways to catch it before it catches you. While attackers may use trusted platforms and real-looking messages, there are always subtle signals. You just need to know what to look for.
Here’s how to stay a step ahead of even the most Gmail sophisticated attacks.
Analyzing URLs
Phishing links in Gmail phishing campaigns are often hosted on services like Google Sites or Forms. But even then, details give them away:
- The Key Indicator: In this specific campaign, the primary red flag was the use of sites.google.com for the fake login portal, instead of the legitimate accounts.google.com domain used for Google account authentication.
- General URL Scrutiny: Beyond this specific indicator, users should always verify the authenticity of URLs before entering credentials. Look for subtle misspellings, unexpected subdomains, or domains that don't match the purported sender. Hovering the mouse cursor over a link (without clicking) can often reveal the true destination URL, which may differ from the displayed link text.
- Beware of shortened or encoded URLs. These are often used to obfuscate the true destination.
Email Header Analysis
Email headers contain a wealth of technical information about the message's origin and path, which can reveal spoofing attempts that bypass basic sender verification.
In Gmail, users can view the full headers by opening the email, clicking the three vertical dots ("more") next to the reply button, and selecting "Show original".
Actually, Nick Johnson, who revealed this specific Gmail phishing email on X, mentioned that looking closely at the headers was one of the first technical signs that something was wrong, even though the email initially looked legitimate.
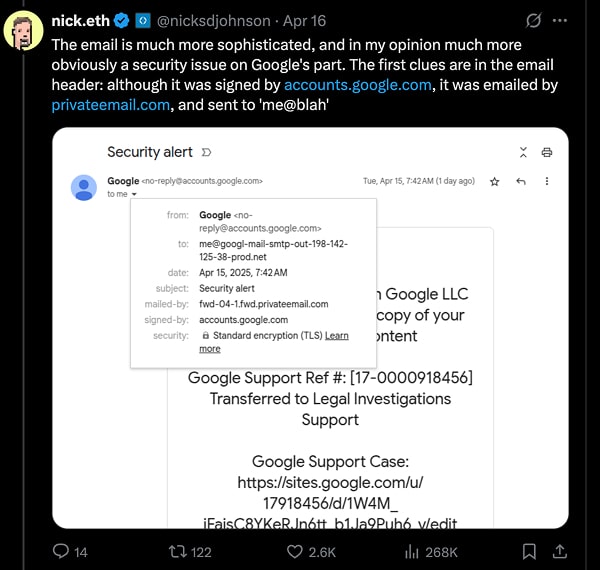
Essential email header analysis for spoofing detection:
Behavioral and Content Indicators
Even the best Gmail phishing attempts have flaws:
- Urgent language: “Immediate action required” or “Final notice before suspension.”
- Mismatched tone: Does the language feel slightly off from a typical Google message?
- Inconsistent branding: Old Google logos, incorrect spacing, or misaligned elements.
- Strange attachments or links asking you to reauthenticate unexpectedly.

Also, ask yourself: Why would Google send you a subpoena or a legal threat via email? Trust your instincts – and verify.
User Defense Blueprint: Immediate and Proactive Measures
Protecting against sophisticated phishing attacks like the Rockfoils campaign requires both immediate actions if compromise is suspected and ongoing proactive security hygiene.
Immediate Actions
If a user suspects they have encountered or fallen victim to this phishing scam, the following steps should be taken immediately:
- Do not engage further: If an email seems suspicious, do not click any links, download attachments, or reply. If a link was clicked but no credentials entered, close the browser tab immediately.
- Check your recent activity: Log into your Gmail and review your account’s login history. Look for unfamiliar IPs, devices, or access times.
- Change your password: Even if you haven't clicked anything suspicious, rotate your password and enable two-factor authentication (2FA) immediately.
- Revoke third-party access: Go to your Google Account > Security > Third-party apps. Revoke anything you don’t recognize or use.
- Report suspicious emails: Use Gmail’s “Report phishing” function for any email that seems off. It helps Google update filters and warn others.
Proactive Measures:
- Use a separate email for sensitive activity: Don’t rely on a single account for everything. Separate personal, financial, and professional email streams.
- Audit your security settings regularly: Set a quarterly reminder to review your recovery methods, app permissions, and device activity.
- Create strong, unique passwords: Use long, complex passwords or passphrases for your Google account and all other online accounts. Never reuse passwords across different services.
- Use password managers: Employ a reputable password manager to generate, store, and automatically fill strong, unique passwords for each site.
- Do an independent verification: The safest approach when receiving a suspicious security alert or request is to never click links within the email. Instead, manually type the official website address (e.g., myaccount.google.com or the service provider's main site) into your browser's address bar and log in directly to check for any genuine notifications or issues.
- Stay informed: Keep abreast of current phishing tactics and security threats.
- Choose a secure email service: Actively consider migrating your primary, sensitive communications to a provider built fundamentally on security and privacy principles.
These aren’t just suggestions – they’re essential survival tactics in today’s email threat landscape. The more attackers mimic trusted systems, the more proactive you must be.
Google’s Response: What Fixes Are Coming (And Are They Enough?)
Google confirmed they were aware of this specific "class of targeted attack" attributed to the threat actor "Rockfoils". They acknowledged that the attack involved a novel exploitation of both Google OAuth and DKIM mechanisms, combined with the abuse of the Google Sites platform to host the phishing pages.
Mitigation Efforts and Timeline
Google communicated that they were actively working to neutralize the threat:
- Protection Rollout: As of mid-April 2025, Google stated they had been "rolling out protections for the past week" specifically targeting this attack vector.
- Full Deployment: They assured that these protections would "soon be fully deployed," which would effectively "shut down this avenue for abuse". While a precise date for full deployment was not provided, the implication was that a fix was imminent.
- Specific Fixes: Google mentioned they were shutting down the mechanism attackers used to insert "arbitrary length text" (likely referring to the manipulation of the OAuth application name to inject phishing content into legitimate alerts). Context from a related Google Workspace incident also mentioned adding detection for authentication bypasses.
But here’s the big question: Will that be enough?
In truth, even the best AI and the sharpest filters can't stop every Gmail phishing attempt – especially not when they come cloaked in Google’s own infrastructure. That's why secure, encrypted email services are becoming not just a preference, but a necessity.
This attack exposed the gaps in mainstream email. Google’s infrastructure – once assumed to be a safety net – was weaponized. The lesson? Don’t rely solely on default protections. Take your security into your own hands and switch to a secure email provider.
Choose Atomic Mail for Ultimate Email Security
Let’s be honest: if Gmail phishing is this effective even within Google’s walled garden, it’s time to rethink what “secure email” actually means.
Mainstream platforms like Gmail were built for convenience and scale – not for unbreakable security. That’s why Gmail sophisticated attacks keep breaking through. These platforms prioritize usability and advertising, not true end-to-end protection.
Secure email services like Atomic Mail take a fundamentally different approach.
Why Choose Atomic Mail?
Atomic Mail was built from the ground up for those who demand uncompromising digital privacy:
- Advanced end-to-end encryption for both internal and external communication. Your messages are encrypted on your device and stay that way through delivery – no matter who you’re emailing.
- Zero-access architecture: Unlike traditional providers, we physically cannot read your messages. No backdoors. No snooping. Ever.
- Anonymous sign-up: Create email without a phone number and any personal details. Just choose your username and go.
- No third-party tracking, no ads: Your inbox is your private space – not a data-mining playground.
- Built-in alias support and seed-phrase recovery: Keep your real identity safe and maintain full access control.
With Atomic Mail, your inbox isn’t just a communication tool – it’s a fortress. It’s not about paranoia. It’s about pragmatism. If attackers are using Google’s own tools to fool you, the only real solution is to remove the tools they rely on.
The truth is simple: if you're still using legacy inboxes as your primary email, you're fighting modern threats with outdated armor. It's time to upgrade. It’s time to take your privacy seriously.
✳️ Sign up for Atomic Mail today and protect your inbox!



