Introduction to the Threat Landscape
Hackers often try to exploit user trust by impersonating well-known brands, and McAfee is a common target. McAfee scam emails are a form of phishing where attackers try to trick you into sharing your personal details.
Cybercriminals use the trusted name McAfee because it's familiar. Lots of people recognise it as a legit antivirus brand, so the scam feels believable. Add in a ticking clock, and the illusion becomes almost irresistible, so even cautious users can be fooled.
And this isn't just about one fake invoice in your spam folder. These scams are part of a bigger, changing threat landscape where attackers use psychology, stolen data, and advanced tech to exploit human weakness. The first step to protecting yourself is knowing how they work.
Inside the McAfee Scam Email
What is McAfee?
McAfee is one of the longest-standing antivirus companies around, and it's well-known for protecting computers from malware, ransomwar, and viruses. It's been used by millions of people over the last 30 years. That's why criminals use the McAfee brand to create fake messages.
What is a Phishing Email?
A phishing email is like digital bait. Attackers pretend to be someone you trust – like a bank, a delivery service, or, in this case, an antivirus provider – to trick you into clicking on links or downloading files. Once you've clicked on the link, they can steal your credit card information, passwords, or even install spyware on your device. The McAfee scam email is just a special kind of phishing, but it's dressed up as an antivirus email.
McAfee Scam Email and Why These Scams Work
Why do so many people fall for them? Because scammers use fear as their primary weapon. A McAfee email scam often claims:
- Your subscription has expired.
- Your computer is infected with a virus.
- You’ll lose protection unless you act immediately.
Fear makes people act quickly. When you see a fake invoice saying you'll be charged $399 today, you probably want to react straight away. And that's exactly what the scammers are counting on.
How Scammers Design Emails to Look Real
These days, phishing isn't sloppy. You probably won't see any broken English or obvious typos. Today's McAfee scam emails look professional and polished, and they often use the latest technologies.
- AI-generated text: Attackers use AI to craft flawless English and even adapt to your region.
- Email spoofing: The “From” field can be faked to look like it’s really coming from McAfee’s official domain.
- Stolen graphics: Logos, layouts, and design elements are copied straight from real McAfee emails.
- Personalized details: Some scams insert your real name, email, or location (data often leaked in previous breaches).
For example, imagine you get an email that looks just like a real receipt, with your name on it and a support number to call. Most people wouldn't suspect it's a fake. That's how precise the McAfee email scam is today, which is pretty scary.
McAfee Scam Email Format
To combat McAfee phishing scams, it's essential to understand their email format. Each component is created to manipulate and deceive.
The "From" Field
So, the 'From' field is where we'll start. Scammers often use a display name that's deceptive, like "McAfee Customer Support", but the underlying email address is a generic one from a public domain like Gmail. A more sophisticated technique involves using a spoofed or lookalike domain with subtle misspellings (e.g., support@mcaffee.com), or extra words (e.g., support@mcafee-alerts.com). You can spot a real message from McAfee because they'll always be from an official domain like these: @mcafee.com.
The Subject Line: Urgency and Fear
The subject line is designed to grab your attention and make you react emotionally straight away, like feeling urgent or scared, and make you act without thinking. There are a few things that come up a lot, like money stuff or problems with security.
Examples include messages that say things like "Payment Success" [sic], "Your subscription is now active," or "BILL No. GGH1644259106OV," and they're all designed to make the recipient worry and get them to fall for the scam.
The Salutation: The Impersonal Greeting as a Red Flag
Normally, legit companies will address users by name. Phishing emails, sent out in bulk, often use generic salutations like "Dear Subscriber," "Dear Customer," or "Hi user." If you get an impersonal greeting, especially in an email about money or security, it's probably a scam.
The Body: Narrative, Flaws, and Manipulation
The email body usually contains the core scam narrative, such as a subscription renewal notice, a fake invoice, or a security warning. The text uses phrases like "act now" and "your account has been charged" to make you feel pressured. In the past, grammatical errors and spelling mistakes were a big red flag, but now that's less true with the rise of AI language models.
Weaker structures, like bad grammar, can also be a way of filtering things on purpose. High-interaction scams take a lot of time to set up. An email with obvious errors gets filtered out by savvy individuals, making sure that only the most impulsive or less cautious targets – the ideal victims – get to the next stage.
The Malicious Payload: Links and Attachments
The goal of most phishing emails is to get the recipient to interact with a malicious payload.
- Malicious Links: Scammers often embed links that look legitimate but actually take you to a dodgy website. They might use URL shorteners to hide where they're actually going. Just hovering the mouse over a link without clicking is a really important technique to show you where it's actually going.
- Weaponized Attachments: Watch out for dodgy attachments pretending to be invoices or receipts, especially the PDF ones. They might download malware, ransomware, or keylogging software on your device.
The Branding: The Uncanny Valley of Forgery
Although scammers often steal official branding, their forgeries are often imperfect. Logos may be low resolution, pixelated or distorted. Phishing emails often lack standard features such as a detailed footer containing contact information and links to the privacy policy, which you would usually find in a legitimate business email.
Types of McAfee Email Scams You Might Face
Although the packaging may change, the poison inside remains the same. Below are the most common variants of the McAfee email scam currently flooding inboxes.
Fake Subscription Renewals
McAfee subscription scam email is the most common version. The victim gets an email that looks like it's from McAfee saying their subscription has been renewed for a large sum, like $240.42 or $499.99. The email looks like a real payment confirmation, and it's got an invoice number on it.
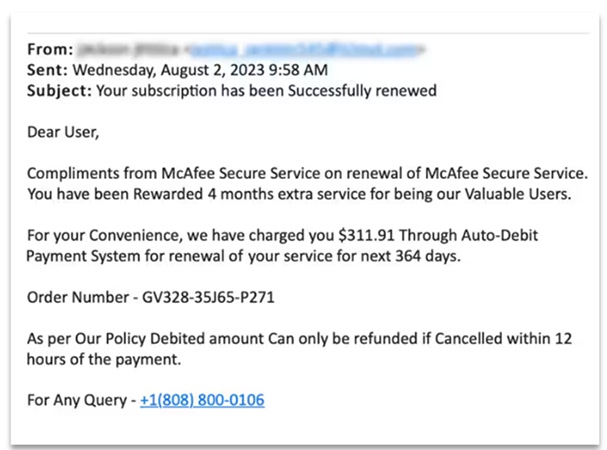
The panic button is pushed: “Wait, I didn’t order this!” The scammers want you to click a cancellation link or call a fake support number, where they’ll grab your payment details.
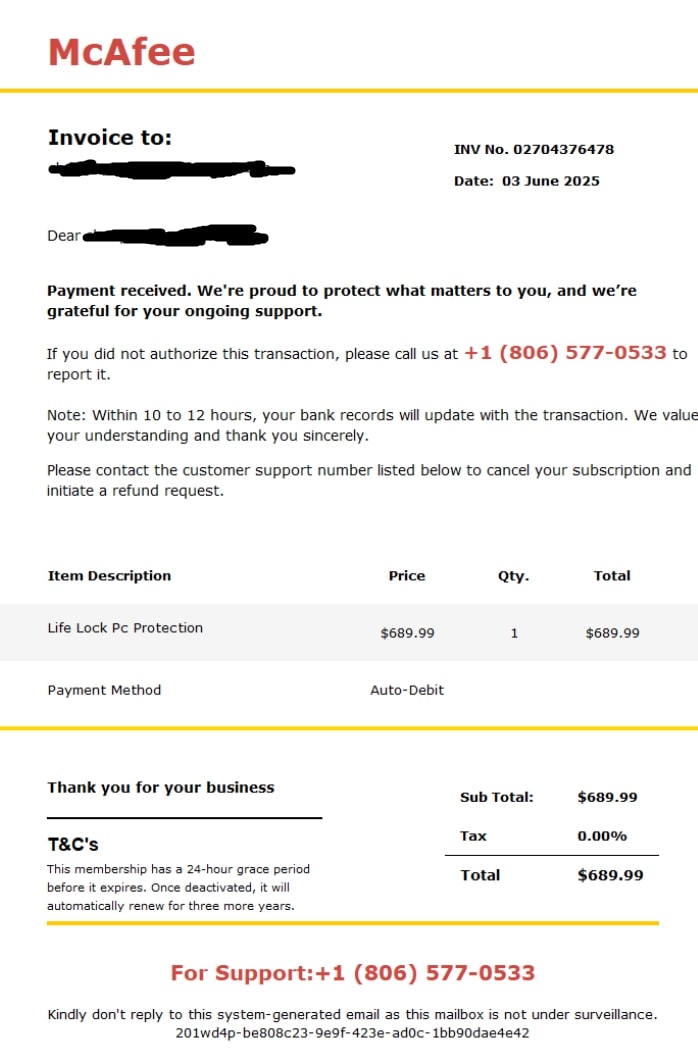
Malware-Laced Invoices & Receipts
Some of the McAfee email scams look like PDF invoices. But instead of a receipt, the attachment hides malware. Opening it can infect your computer, giving attackers full control or stealing your sensitive files.
Virus Alert
This is pure, uncut scareware. The email claims that a "critical virus", like Trojan or Pegasus, has been detected on your device through a "remote scan". It's nonsense, of course – your email can't scan your computer, but the fear it creates is real.
There'll probably be a big button that says "Remove Threat Now" or "Run Full System Scan." Clicking on it can actually do the opposite of what it's supposed to do – it'll download the very virus or take you to a phishing page.
Tech Support Hoaxes / Compromised Account Alerts
This McAfee scam email makes out it's a security alert about some suspicious activity on your account, and it's got you in a state of panic. Then it takes you to a fake login page for McAfee that's designed to steal your details, or a support number that's not real and where the scammers will try to get into your computer remotely. Either way, the end result is the same: your account and personal data will be compromised.
Refund / Chargeback Traps
A clever piece of reverse psychology. It says: “You’ve been mistakenly charged $399 — claim your refund now.” Who doesn't want free money? Of course, the refund link takes you to a phishing site that'll steal your bank details, or they'll ask you to fill in a form with your credit card info. Instead of a refund, you get robbed.
How to Detect a McAfee Scam Email Instantly
Spotting a McAfee email scam isn’t always obvious, but you don't need to be a cybersecurity expert to defend yourself. All you need to do is use your digital detective skills. You'll learn to look past the surface and spot the tells. These techniques will help you spot 99% of phishing attacks.
1. Subtle Signs in Sender Address
Click on the “From” field. Scammers often mask their real address with something similar to a legitimate one.
- A real McAfee email will come from their real simple domain like @mcafee.com.
- A McAfee scam email will use tricky lookalike domains. For example:
- support@mcafee-security-alerts.com (They registered a different domain)
- billing@mcafeesubscriptions.net (They used the wrong Top-Level Domain, .net instead of .com)
- no-reply@mail.mcafee.co (They are trying to imitate a subdomain, but the core domain is .co, not .com)
Note: This list is based on information provided by McAfee and is subject to change. Always verify suspicious communications through the official McAfee website.
However, a sophisticated scammer can even forge the visible "From" address. This is called spoofing. To unmask a spoofed email, view the email's original source or header via your email client's options menu (e.g., Gmail's "Show original"). In the code, find the Authentication-Results section and check the status for security protocols like SPF, DKIM, and DMARC. If any of these show a FAIL status, you have definitively proven the sender's address is forged and the email is fraudulent.
2. The “Hover to Reveal” Technique
Never click links blindly. Hover your mouse over the link to see the real URL. If it doesn’t lead to mcafee.com but instead to a random string of characters or unfamiliar domain, it’s a trap.
The golden rule: if you're ever unsure about an account, just close the email. Open your web browser and type in the official website you need (in this case, www.mcafee.com) and log in. Any legit notifications will be waiting for you in your account dashboard.
3. Missing Personal Touch
A lot of McAfee scam emails still start with 'Dear Customer' instead of your name. Real services usually know your name or account details, so generic greetings are a common red flag.
However, be warned: scammers are getting smarter all the time. Because of all the data breaches, it's now common for a McAfee email scam to address you by your real name. So, while a generic greeting is still a big red flag, a personal one isn't a sign of legitimacy. You've got to rely on the other checks too.
Key Red Flags to Watch Out For
- An intense sense of urgency or threats: "Your account will be terminated," "Immediate action required!"
- Poor grammar or strange wording (though AI is making this less common)
- Unexpected attachments
- Phone numbers and email addresses that don’t match the official McAfee site
- Suspicious links hidden behind “Click Here”
- Requests for personal information – no real company will ever email you asking you to click a link to "verify" your password, credit card number, or home address.
When in doubt, don't interact; go directly to the company's official website and contact support to ask if they genuinely sent you a message.
What To Do If You Receive One
If you get a McAfee scam email, you might panic or delete it straight away. Don't do that. Take a breath and follow this simple, safe procedure to neutralise the threat and help protect others.
Step-by-Step: Don’t Click, Verify, Delete
- Don’t click anything – not links, not attachments.
- Verify independently – if you’re worried, go to the official McAfee website manually or check your actual subscription status.
- Report – before deleting, report the email. This is a crucial step that helps email providers and authorities shut these operations down. (More on this below).
- Delete and block – keeping the email in your inbox increases the risk of accidental clicks later.
Immediate Actions for Victims
If you suspect you have compromised your information, act immediately.
- If credentials were entered – change your password immediately on the legitimate website and on any other account where you have reused it.
- If financial information was shared – contact your bank or credit card company to report the fraud, cancel compromised cards, and monitor your statements.
- If remote access was granted – disconnect the device from the internet immediately. Run a full scan with reputable antivirus software before reconnecting.
Reporting to McAfee, Your Email Provider, and Authorities
- Forward the scam to: phishing@mcafee.com.
- Report it via your email client (Gmail, Outlook, etc. have “Report Phishing” buttons). This action is vital as it trains the platform's filters to better recognise and block this McAfee scam email in the future.
- In the US, you can also forward phishing attempts to the Anti-Phishing Working Group at reportphishing@apwg.org.
- Internet Crime Complaint Center (IC3): If you have suffered a financial loss, file a complaint with the IC3, a partnership between the FBI and the National White Collar Crime Center.
Reporting matters. Each report helps security teams shut down scam infrastructure and warn others.
Choose Atomic Mail: Security Beyond “Spam Filters”
Most providers fight phishing with filters, but they rely heavily on profiling your data for advertising. This means more data exposure, and, ironically, more personalised scam attempts.
A private, encrypted service like Atomic Mail doesn't scan or sell your data – and that puts a stop to scammers. We built our service from the ground up to be as private and secure as possible against the latest online threats.
Why Atomic Mail is Different
- End-to-end encryption: Only you and your recipient can read the message.
- Zero-access privacy: We cannot profile or read your data – even if we wanted to.
- Alias addresses: Shield your real inbox by creating additional email addresses.
- Anonymous sign-up: No phone number or additional email required.
- AI-based spam filters: Smarter detection that adapts to modern phishing tricks.
- Self-destructing messages: Sensitive emails can be set to automatically delete after a certain time.
- GDPR compliance: Your data rights are respected by design, not as an afterthought.
Atomic Mail doesn't just stop scams, it changes the rules. With us, your inbox is your best defence, not your biggest weakness.
👉 Ready to make the switch? Protect yourself today – sign up for Atomic Mail for free.



