TL;DR: Welcome To The Checkpoint Internet
Age verification is turning the internet into a place where you prove who you are before you read, watch, post, or even install an app.
- Age verification law is spreading. More places now treat ordinary browsing like a restricted purchase.
- Governments claim this is to protect children. But the technology required to enforce these rules builds a surveillance infrastructure that tracks everyone, regardless of age.
- The typical age verification system boils down to two doors: ID upload or face scan.
- Either door creates a new data trail: your offline identity ↔ your online behavior.
- The risks are high. This data gets breached, misused, resold, subpoenaed, and quietly repurposed.
- You don’t need to be doing anything “shady” to get hurt. You just need to be human.
If you value your privacy, you need to understand what is happening.
What Is “Age Verification / Age Estimation / Age-Gating”
Historically, child safety online focused on filtering content (e.g., blocking pornography). The new wave of regulations focuses on filtering people. This is a critical distinction.
- Age assurance is the process of verifying whether someone is old enough to use digital services. The three main methods of doing this are age-gating, age estimation and age verification:
- Age gating is the traditional model, such as the 'I am 18+' button found on websites. It is a self-declaration method that relies on users being honest about their age, so it is not always accurate.
- Age estimation technologies triy to use biometric or behavioral signals to predict age without necessarily knowing the user's legal identity.
- Age verification requires hard proof. An age verification system demands you prove who you are to prove how old you are. This usually means uploading a government-issued ID or a credit card.
The result is the same, whether it's a hard check or a soft guess: you are identified, processed and judged before you can load a webpage.
What age verification is trying to control
The target isn’t only pornography and adult content. Age verification law regularly expands to:
- social platforms
- app stores
- community forums
- gaming and chat features
- content categories that governments label “harmful” or “sensitive” (which can grow fast)
When the gate is built, the list of “things behind the gate” tends to grow.
Why Governments And Platforms Are Pushing It Now
Age verification is often sold as a means of protecting children. Sometimes that’s genuine, but often it’s just marketing or politics. Either way, the motivations are clear.
Official reasons
1) “Protect children online.”
The public narrative is powerful and emotional. Politicians and pressure groups argue that social media, gaming, and adult sites are dangerous environment for children. They want to ptevent kids from viewing harmful content or being contacted by predators.
But child-safety outcomes are not the same as child-safety gestures. EFF’s position is clear: age gates do not protect children, nor do they magically fix the underlying harms; in fact, they can create new ones.
2) “Duty of care” pressure.
Laws like the UK’s Online Safety Act or the various U.S. state bills and proposals are presented as a "duty of care." The aim is to proactively reduce “harms,” so platforms reach for something measurable.
Age verification becomes that measurable lever: “We verified the age, therefore we complied.”
3) One standard instead of chaos.
Even supporters admit the patchwork is a mess. The pragmatic argument is that age verification should be centralized at the app store level to make it 'simpler'. Simple for whom, though?
The App Store Accountability Act (proposed US legislation) has attracted broad national backing, with support from Pinterest, the Digital Childhood Alliance, Heritage Action, the International Union of Police Associations, and more than 150 child-safety organizations and advocacy groups.
Hidden reasons
1) Liability shifting
Age verification law often turns into a hot potato. Platforms don’t want to be blamed for what kids see, so they push age verification onto a verification vendor.
If a kid gets through, they can blame the third-party vendor or the user for "lying," rather than their own addictive algorithms. This shifts the responsibility from the trillion-dollar company to you.
2) A surveillance dividend
Age verification systems don’t just answer “are you 18+?” They create infrastructure to answer:
- who you are
- where you are
- what you looked at
- what you tried to access
- when you did it
- on what device
That is a surveillance system, even when nobody calls it that.
3) A censorship lever that doesn’t look like censorship
Age-gating is a powerful tool because it can be framed as “safety,” while still blocking lawful content: tt doesn’t need to ban speech, it just needs to make speech hard to reach. EFF has written about how age gates can become expressive-rights nightmares, far beyond adult content.
4) Ending encryption by proxy
Governments hate encryption because it prevents them from seeing what you say. If they can't break the encryption, they can at least force you to identify yourself before you say it. An age verification law is a convenient backdoor to de-anonymize the web without explicitly banning encryption.
5) A moat for big players
Big platforms are already in constant conversation with regulators, which makes them the “safe bet” for governments: predictable, compliant, easy to pressure. Smaller services (especially privacy-first ones) are harder to control and less interested in building surveillance hooks. So when an expensive age verification system becomes mandatory, the result is unequal: the giants absorb it, while smaller providers either pay a vendor tax, take legal risk, or shut features down.
How Age Verification Works
To comply with diverse global mandates, platforms now employ a 'stack' of verification technologies.
Government ID upload (passport / driver’s license): You upload a photo of your ID (usually to a third-party vendor, like Persona, Veriff, SheerID, etc.). They read your details, validate the document, and send the site a “pass/fail” result.
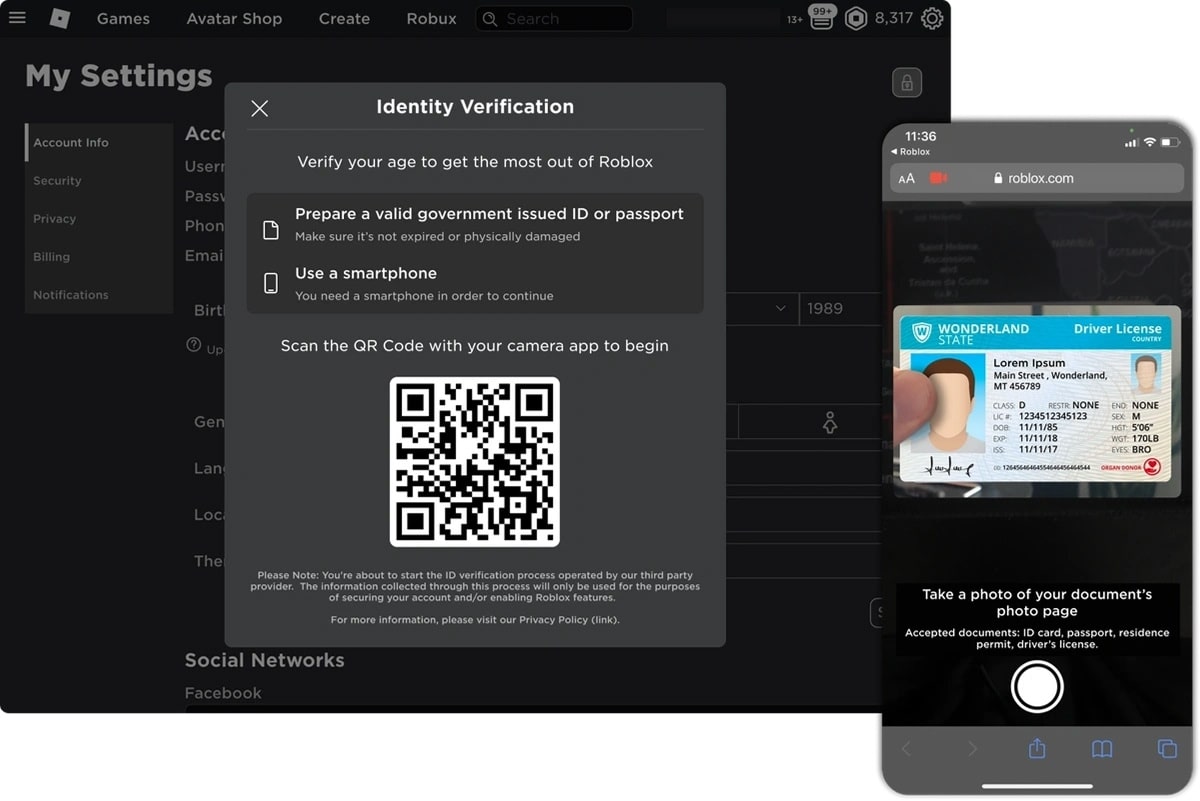
Biometric “face scan” + liveness checks: You record a selfie or short video, then do “liveness” prompts (blink, turn, smile). The system checks you’re real (not a photo) and match your face to an ID.
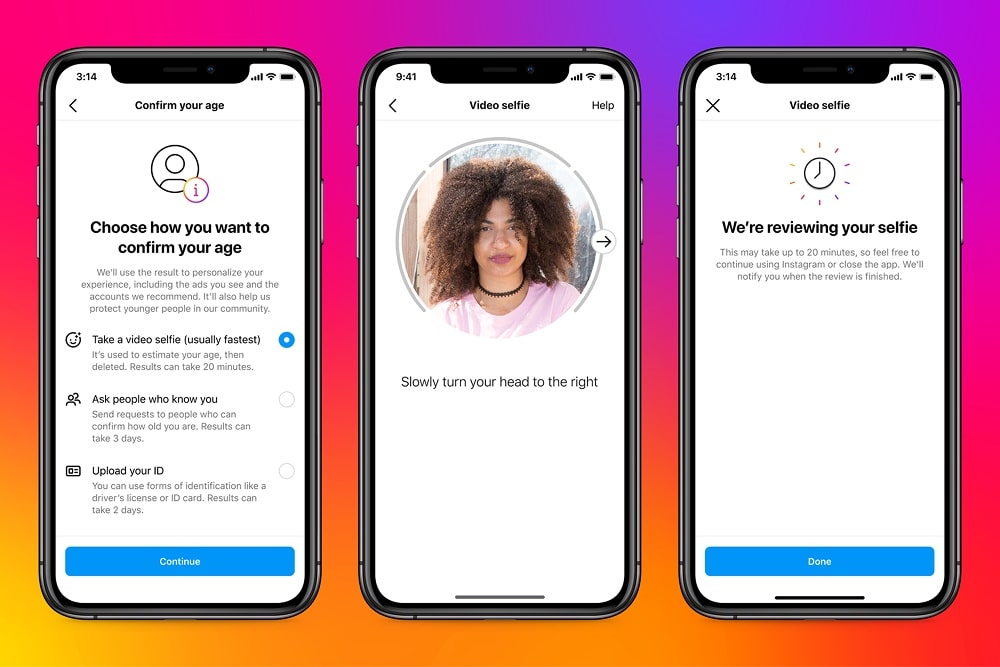
AI age estimation (no ID, still biometrics): You look into the camera, and an AI guesses your age based on biometric markers, like skin texture, eye shape, face proportions. However, these systems fail in predictable ways. People close to the threshold (16-19) get misclassified, some groups face higher error rates, and when an algorithm decides you’re “too young,” you’re often stuck arguing with a bot.
Credit card / financial checks: The site charges a nominal fee (or just checks the validity) of a credit card. However, it assumes every adult has a credit card (millions don't) and creates a financial paper trail for your browsing habits.
App Store level age checks: This is the model Pinterest recently endorsed. Instead of every app asking for your ID, Apple or Google verifies you once at the device level. This turns Apple and Google into the ultimate internet police.
"Soft" age signals: This is the invisible surveillance. Platforms analyze your "digital exhaust" – what apps you have installed, how fast you type, what slang you use in search queries, your location history.
Zero-knowledge proofs (ZKPs): The privacy-ideal: prove “I’m 18+” without revealing your birthdate or name. It’s still mostly pilots/experiments (including EU mini wallet pilot and Cloudflare’s efforts) and not widely adopted yet.
No matter which method is used, the outcome tends to be the same: your access gets logged, your identity gets correlated, and you’re still tracked.
Where It’s Already Landing: Laws And Rollouts
Age verification law is already live in multiple places, and the pattern is repeating: a new rule arrives → platforms panic → an age verification system is hastily implemented → users pay the privacy bill.
- Australia: The "world-first" social media ban. Australia’s social media minimum age framework (16+) started in December 10, 2025. Platforms must take “reasonable steps” to prevent under‑16s from holding accounts, which pushes age verification into everyday sign-ups and logins.
- The UK: The UK’s Online Safety Act (began in January 2025) is already forcing stronger age checks in practice, especially around adult content.
- The US: The mess is state-by-state. Few high-signal examples:
- Federal (KOSA): The Kids Online Safety Act passed the Senate in July 2024 but stalled in the House through Dec 2025; it was reintroduced in May 2025 but has not become federal law.
- Supreme Court Ruling: In June 2025, the Supreme Court upheld Texas law HB 1181 in Free Speech Coalition v. Paxton. The court ruled that age verification for pornographic content does not violate the First Amendment, validating ID checks in states like Texas, Louisiana, and Utah.
- State Patchwork: More than 20 states now enforce AV laws for adult content, while social media laws, such as Ohio's, face tougher constitutional challenges in lower courts.
- The EU: Moving slowly but systematically.
- The Digital Services Act (DSA) guidelines released late 2025 push for age verification on high-risk platforms.
- eIDAS 2.0: The EU is rolling out a Digital Identity Wallet. A prototype "age verification app" (mini-wallet) is being piloted in 5 countries to allow interoperable, privacy-preserving checks across the bloc.
- China: China is the “mature baseline” for these systems. Its Age Verification System is a government-mandated infrastructure that restricts minors' access to online games and digital platforms. All users in China must undergo “Real Name Verification” before accessing gaming services. Once the system knows your age, restrictions can be enforced automatically.
Recent Examples: Who Is Watching You Already?
Social & communities
- YouTube: Expanded AI-based age estimation to the US, EU, and Australia.
- Discord: "One-time" age assurance required for UK and Australian users to access NSFW servers or disable sensitive media filters.
- And the nightmare scenario happened: A third-party vendor was hacked, and over 70,000 images of government IDs (passports, driver's licenses) were leaked.
- Spotify: facial age check, with an ID verification fallback if the estimate is wrong.
Gaming
- Roblox: moving chat behind facial age estimation. Not “optional parental controls.” A core feature increasingly tied to age verification.
- HoYoverse: US players required to age verify accounts with clear deadlines; accounts can be restricted/suspended if the age verification system isn’t completed.
Risks And Dangers of Age Verification
Age verification isn’t one risk. It’s a stack of risks, from technical and legal to social, because an age verification system is a data system.
- Privacy (identity linkage + “forever data”): IDs and biometrics don’t expire and change the way passwords do. Age verification systems create massive centralized databases of IDs linked to user behaviors. It’s a honeypot for hackers.
- Security (breach blast radius): one vendor breach can expose ID photos at scale. Discord’s third‑party incident is the exact shape of the problem.
- Discrimination & false rejections: AI estimation is less accurate for people of color, people near 18, and those with facial differences, leading to higher rejection rates for these groups.
- Adults without IDs or credit cards get locked out: in the name of safety, we are blinding the youth. By age-gating the web, we block young people from essential resources: mental health support, objective sex education, and support communities.
- Young people lose access to essential information: age gates and parental-consent flows can block minors from sex education, mental health resources, and support communities – exactly the stuff they often can’t safely ask for offline.
- Chilling effects on lawful speech: people don’t research, read, join, or ask when doing so requires age verification. It’s not just porn. It’s health, identity, education, support.
- Circumvention arms race: VPNs rise, workarounds multiply, lawmakers respond with tighter age verification law drafts, and the checks get more invasive. Ofcom has already mentioned VPN spikes after UK age checks.
- The death of anonymity: we are losing the right to exist online without a paper trail. We are moving from a "permissionless" internet to a "permissioned" one. If we accept this, the private, open web is dead.
What You Can Do About It
You can’t personally stop every age verification law, but you can make yourself a smaller, harder target.
1) Minimize what you hand over and where
Every time a site asks for your birthday, phone number, or real name, ask yourself: Do they actually need this? If it’s optional, leave it blank.
2) Separate identities across services
Don’t use one identity everywhere. Split email addresses/aliases by category (apps, social, gaming, subscriptions, sensitive accounts) to reduce correlation.
Never use "Log in with Google" or "Log in with Facebook." It links your activity across the web into one giant, trackable profile.
3) Protect recovery channels
Set a carrier port‑out PIN, avoid SMS 2FA, use an authenticator/hardware key, and lock down your primary email.
4) Don’t share ID scans/biometrics unless truly necessary
Before any age verification prompt, check who’s collecting it (site vs vendor), what they store, and how long. If the only option is “ID + face scan,” decide if it’s worth it.
Do not upload selfies or ID scans unless it is absolutely critical.
5) Secure receipts and “verification” emails
Age gates generate receipts, appeal links, and “verify again” notices – prime phishing bait. Keep that inbox private and hardened.
6) Use a VPN (a good one)
A VPN can reduce ISP-level visibility and help in some regions, but it’s not magic. Choose a reputable provider with a strong no‑logs stance and modern protocols.
7) Avoid Big Tech when you can
Swap to privacy-first tools where it matters most:
- Email: Swap the data-mining Gmail/Outlook for a private, encrypted email like Atomic Mail.
- Passwords: Stop using Google Password Manager. Switch to a dedicated, open-source manager like Bitwarden.
- Social media: Leave the algorithm-driven surveillance of X (Twitter) or Facebook for decentralized platforms like Mastodon.
- Messengers: Drop WhatsApp (owned by Meta) for Signal, the gold standard in encrypted messaging.
- Browsing: Use Brave with strict privacy settings, not Chrome.
8) Support the fight for a better internet
Support organizations like the EFF (Electronic Frontier Foundation) that are fighting these unconstitutional mandates in court. Help the privacy ecosystem grow by rating and reviewing secure services – your voice helps others find alternatives. And most importantly, spread awareness: tell your friends why their privacy matters before it's gone.
Atomic Mail Angle: Protecting Your Identity When The Internet Demands More Of It
We built Atomic Mail for one reason: to protect your right to communicate without surveillance.
We don't know who you are: We don't ask for your phone number. We don't want your ID. We don't scan your face. You can create an account in seconds, anonymously.
We can't read your mail: Our end-to-end and zero-access encryption means even we cannot access your encrypted messages.
We don't sell you out: You are our client, not our product. No ads, no tracking, no behavioral profiling.
✳️ Sign up for free today and get: encrypted email, multiple aliases, private seed phrase recovery, and a calmer online life – especially as age verification becomes the default gate.
FAQ: Age Verification
What is age verification?
Age verification is any process that tries to confirm you’re above a legal age (often 16 or 18) before you can access content or features, usually via an ID check, a face scan, or other “age assurance” signals.
How does age verification work online?
Most platforms pick one of these: ID upload, biometric face scan + liveness, AI age estimation, credit-card/transaction checks, or app store-level age gates that pass an “age signal” to apps.
Is age verification safe?
Generally, no. Age verification systems require sensitive, often permanent data (ID images, biometrics). That data can be mishandled or breached. There’s already a case where a third-party hack has exposed over 70,000 Discord users’ ID photos.
What states require age verification for adult content in the US?
As of late 2025, Free Speech Coalition tracks laws in effect for adult sites in: Alabama, Arizona, Arkansas, Florida, Georgia, Idaho, Indiana, Kansas, Kentucky, Louisiana, Mississippi, Missouri (effective Nov 30, 2025), Montana, Nebraska, North Carolina, North Dakota, Ohio, Oklahoma, South Carolina, South Dakota, Tennessee, Texas, Utah, Virginia, Wyoming.
Latest tracker (always changing): https://action.freespeechcoalition.com/age-verification-resources/state-avs-laws/
Will age verification apply to everyone or just kids?
While the laws target children, the technology requires everyone to be verified to distinguish adults from minors. Therefore, adults must prove their age to access restricted spaces.
How to bypass age verification?
We can’t help with evading age verification law or defeating an age verification system. Some people try VPNs or incognito/private browsing (you’ll see this discussed around YouTube), but there’s no single effective solution – platforms and laws adapt, and “quick fixes” can push you toward sketchier sites and riskier verification flows.
Does age estimation mean “no data collected”?
No. “Age estimation” usually means biometrics (a selfie/video analyzed by AI). It can still be stored, breached, or reused, and it’s often wrong near the cutoff.
What should I do if a site asks for my ID or face scan?
If possible, don’t provide it. If you absolutely must proceed, check who the verification vendor is, choose the least invasive method available, and decide if the content is worth linking to your identity. Share the minimum, and don’t reuse the same email identity everywhere.
Does Atomic Mail require age verification?
No. We do not ask for your age, ID, or phone number. We believe in the right to communicate anonymously. Our architecture is built to protect your identity, not verify it.



